
Regular Issue, Vol. 11 N. 2 (2022), 159-178
eISSN: 2255-2863
DOI: https://doi.org/10.14201/adcaij.27271
 |
ADCAIJ: Advances in Distributed Computing and Artificial Intelligence Journal
Regular Issue, Vol. 11 N. 2 (2022), 159-178 eISSN: 2255-2863 DOI: https://doi.org/10.14201/adcaij.27271 |
CHOP: Maximum Coverage Optimization and Resolve Hole Healing Problem using Sleep and Wake-up Technique for WSN
Vipul Narayan and A.K. Daniel
Department of Computer Science and Engineering, Madan Mohan Malaviya University of Technology, Gorakhpur, U.P, India, 273008
vipulupsainian2470@gmail.com, danielak@rediffmail.com
ABSTRACT
The Sensor Nodes (SN) play an important role in various hazardous applications environments such as military surveillance, forests, battlefield, etc. The Wireless Sensor Network (WSN) comprised multiple numbers of sensor nodes which are used to perform sensing the physical conditions and subsequently transmitting data to the Base Station (BS). The nodes have limited batteries. The random distribution of nodes in the hazardous areas causes overlapping of nodes and coverage hole issues in the network. The Coverage Optimization and Resolve Hole Healing (CHOP) Protocol is proposed to optimize the network's overlapping and resolve the coverage hole problem. The working phases of the proposed protocol are network initialization, formation of the cluster, Selection of Cluster Head, and sleep and wake-up phase. The issues are optimized, and maximum coverage is achieved for a specific sensing range. Using statistics and probability theory, a link is established between the radius of the node and the coverage area. The protocol used the sleep and wake phase to select optimal nodes active to achieve maximum coverage. The proposed protocol outperformed and showed improvements in the network's performance and lifetime compared to LEACH, TEEN, SEP, and DEEC protocols.
KEYWORDS
sensor nodes; coverage area; network area; quality of services; coverage hole
1. Introduction
The sensor network domains such as industry, defense, research Wireless Sensor Network (WSN) is widely used nowadays. The sensor networks are randomly deployed in the monitoring area to gather the environmental data and then transmit the collected data to the Base Station (BS). In (Farhat et al., 2018), the authors discussed that the sensor nodes in the network work collectively and autonomously. The coverage is the important metrics for Quality of Service (QoS) in WSN to enhance network lifetime. In (Gupta and Jha, 2019), the authors discussed the limitation of the protocol in terms of the sensing range of the nodes. They have also addressed that coverage and connective are significant issues in deploying the nodes in the sensing area and proposed the Biogeography-based optimization (BBO) technique to optimize the problem. The proposed approach is based on an encoding technique with objective function to optimize the problem occurred in the network. In (Singh et al., 2020), authors discussed due to the impact on the network performance, the authors categorized the coverage problem. Based on the frequency monitored in the network area, there are two categories: sweep coverage and continuous coverage problem. In (Rai and Daruwala, 2016) discussed deterministic and probabilistic sensing models are based on the SN's sensing capacity. The sensing models are further classified into unidirectional and omnidirectional models. The unidirectional sensing model has a finite viewing angle; hence, it does not cover and detect the entire area. The omnidirectional nodes detect the whole area. In (Wang et al., 2015; Aliouane et al., 2016), discussed the mobility model based on Sensor Location Awareness (SLA), sensor sensing range, sensor deployment strategy, which is a very important factor to build a model for coverage protocols. The optimal resource utilization and a hierarchical-based architecture are the essential requirements to perform sensing tasks in the network. Node clustering is the technique where nodes are grouped into multiple classes with similar properties. The data is transferred from Cluster Members (CM) to the respective cluster head (CH), from where it is further finally transferred to the base station. The sensing range adjustment is a crucial strategy for efficient energy utilization in the network. The time between node sensed the data and finally successfully transmitted to BS is known as network lifetime.
The Coverage Optimization and Resolve Hole Healing (CHOP) Protocol is proposed, and the performance is compared for network lifetime and performance of the system. The protocol achieves enhanced network lifetime and transmits more packets to BS.
The rest of the papers are structured as follows: Related work is discussed in Section 2. The proposed Coverage Optimization and Resolve Hole Healing (CHOP) Protocol is discussed in Section 3. The simulation results and validation are deliberated in Section 4. The paper concludes with future directions in the last section.
2. Related Work
The WSN has emerged as a key study area in the domain of artificial intelligence and cloud computing other related fields. In (Nayak et al., 2021), the authors have tried to enhance the Quality-of-Service metrics in WSN. The complexity of the algorithm is unclear that must be computed for practical implementation of the algorithm. In (Narayan and Daniel, 2021), the authors, the deployment of SN throughout the network region is a random process. The CH gathers data and forwards it to the station node. In (Narayan, Daniel and Rai, 2020), the authors suggested the Energy Efficient Two-Tier Region protocol for the data transmission within the network. The capacity to conduct activities utilizing the available Residual Energy (RE) of node and CH nodes. The protocol boosts system efficiency and network stability in terms of lifetime.
In (Prusty, Sethi and Nayak, 2020), the authors focused on a network's route optimization protocol and addressed the issue related to non-uniform distribution of energy, which causes coverage gaps and poor network performance. The technique of movable nodes is used to fix these complex issues. In (Dwivedi, Sharma and Mehra, 2020), the authors devised an Energy Efficient two-stage routing protocol based on the higher residual node is selected as the CH for a specific round. This protocol increased system performance and node RE. In (Ramluckun and Bassoo, 2018), the authors discussed the significance of optimization algorithms in the identification of proper CH based on the route optimization strategy based following metrics on energy consumption, Cluster size, cluster distance, and a total number of clusters created. In (Wang et al., 2010), the authors introduce a protocol for area-aware coverage. The protocol employs SNs with sensing ranges and customizable transmission. The sleep and wake-up methodology is utilized to allocate the duty cycle to each node. In (Shi, Chen and Lin, 2015), the authors have utilized the α-k coverage approach is used to cover the target region with possibility by k nodes. The method maintains some SN active in order to complete the task in the network. The protocol optimizes energy usage and increases network longevity.
In (Narayan and Daniel, 2019), the authors devised a strategy to reduce the network's overlapping issue. For total coverage, the radius of the nodes and RE are chosen as parameters. The protocol mitigates the overlapping problem, and the overlapped SN is used to increase network longevity via the sleep and wake-up mechanism. In (Salam and Hossen, 2020), The authors devised the LEACH (Low Energy Adaptive Clustering Hierarchy) technique, which works best for homogeneous nodes. The restrictions of a protocol are routing, CH selection, data transfer, and aggregation. In (Behera, Samal and Mohapatra, 2018), The authors described the LEACH protocol feature in which every node has an equal chance of becoming CH. Because the protocol uses a single hop for data transfer duties in the network, it requires more energy. The effective use of energy remains a difficult challenge in the network. In (Al-Shalabi, Ababneh and Abdulraheem, 2021), the authors presented the energy hole removal method to solve the energy hole issue. The sleep and wake-up method conserves the power of SNs. The threshold value is used to determine the SN's available and RE for the data transmission operation.
In (Aliouat and Harous, 2012), the authors recommended two Threshold Sensitive Energy Efficient Sensor Network (TEEN) protocol variations (WBM-TEEN and WB-TEEN). Each SN connects with its neighboring SN in the cluster, reducing the number of data packets delivered and received in the network. WB-TEEN and WBM-TEEN outperformed the TEEN and LEACH protocols in terms of lifespan. In (Mittal, Singh and Sohi, 2017), the authors proposed an application-specific low power consuming routing protocol that employs (distance between RE and CHs, distance from BS) as CH selection parameters. When compared to LEACH protocol versions, the protocol outperforms them. In (Peng et al., 2015), The authors presented a scalable clustering technique (ESCS) and an energy-aware and for WSN. The method is based on the notion of the Barabasi-Albert (BA) model. The CH is chosen depending on the network architecture and the SN's energy. The ESCS simulation result improves the scalability period and network lifespan. In (El Handri and Idrissi, 2020), The Node Rank Algorithm (NRA) was proposed by the authors. The NRA selects CH based on the number of linkages within SN and the path's cost. The NRA algorithm has solved the problem of the conventional CH selection procedure, which caused unanticipated CH failure in the previous LEACH version. The NRA outperforms several variants of the LEACH protocols in terms of performance and network longevity. In (Cai et al., 2019), The authors suggested a sensor network routing technique. Data packet transfer requires a lot of energy in the network. To reduce data transmission in the network, the approach utilizes both clustering methods and multi-hop routing. In (Luo and Fu, 2017), The authors explored certain clustering algorithms that need the position of SN to be determined using the Global Positioning System (GPS). However, owing to GPS's high energy consumption and expense, the GPS position is not constantly accessible. The authors proposed a hybrid clustering and routing system that use both qualitative binary data connection and quantitative location data.
In (Singh and Malik, 2017), The authors introduced a sensor network Stable Election Protocol (SEP). It has a two-level architecture and utilizes Normal Nodes (NN) and Advance Nodes (AN). The SEP protocol's CH election probability depends on Initial Energy. The protocol outperforms the LEACH protocol in terms of network stability. In (Nehra, Sharma and Tripathi, 2020), The authors developed the distributed Energy Efficient Clustering (DEEC) routing protocol. The technique allows for multilayer heterogeneity. In multilayer heterogeneity, the SN energy is distributed randomly in a specified energy gap. For the CH selection procedure, the DEEC protocol employs the probability ratio between the RE of each SN and the network estimated average energy. DEEC, when compared to LEACH and SEP, increases network longevity.
In (Chaturvedi and Daniel, 2017), the authors presented a sleep/wake-up methodology for network coverage issues. For trust computation, the protocol's CH selection employs distance, RE, and node as parameters. The protocol outperforms the Disjoint Set Cover (DSC) protocol. In (Khan et al., 2020), the authors introduced the connectivity and energy efficiency algorithm. The few SN are utilized to monitor the data, while the rest of the nodes are retained in sleep mode for future usage and increased network longevity. In (Harizan and Kuila, 2019), the authors recommend the sleep and wake-up strategy. Each node in the network is allotted a timeframe for performing the operation. In a decentralized method, each node freely decides its actions in the specified time frame. The technique implementation performance of the suggested strategy increases network longevity. In (Zimmerling, Mottola and Santini, 2020), the authors presented a method for monitoring network node density. To increase network performance, the reinforcement learning approach allows certain nodes to sleep while others remain active. In (Nithya and Jegadeeshwari, 2019), the authors proposed the Energy-Efficient Scheduling with Deep Reinforcement (E2S-DRL) method. The technique operates in stages to reduce network latency. In the first step, zonal-based clustering is employed for data gathering. The DRL method is utilized in the second phase to award a duty cycle to each node, and routing is accomplished in the third phase utilizing Optimization techniques.
The authors (Rajawat, Jain and Barhanpurkar, 2021) proposed a multi-level-based data fusion protocol for clustering, which is used to increase the coverage area and increase the reliability of the sensor network. The concept of the static sensor is used as a point of interest so that the given area is covered. The two key performance indicators are coverage ratio and network lifetime. The performance analysis showed that using minimum active nodes in the network increases network lifetime. The authors (Al-Fuhaidi et al., 2020) proposed a protocol for maximizing the coverage in the network and minimizing the number of nodes deployed in a given field of interest to overcome the issue of high energy consumption and cost. The proposed protocol used a Probabilistic Sensing Model (PSM) in contrast with the Harmony Search Algorithm (HSA) to balance the network coverage and deployment cost. The HSA works in the protocol to achieve maximum coverage with a minimum number of sensor nodes in the network. The probabilistic sensing model (PSM) is used to deploy the nodes in the network efficiently. The proposed protocol is simulated for a small area where the coverage is almost 100% and the deployment cost is reduced by nearly 50%. The comparative analysis with other protocols achieved the deployment cost reduced by a factor of 10%. In the future, the protocol will be enhanced to simulate a large field of interest. The authors (Nandagopal and Ramesh, 2020) proposed an Optimal Minimum Covering Spanning Tree (OMST) protocol to select the optimal path for data transmission in the WSN. The concept of polling points is proposed in the protocol for enhanced data gathering and reduced time for a data packet to reach the sync node. Low Energy Adaptive Clustering Hierarchy (LEACH) is the two-level clustering protocol. The complexity of the generated tree in the deployment area is reduced using the Particle Gene Swarm (PGS) optimization technique in the protocol. Different performance metrics such as energy, delay, overhead, delivery ratio is used to simulate the performance enhancement over other existing protocols. Optimal path selection in the generated tree is used in the protocol to be overcome for high-performance WSN. The authors(Chen, Xu and Wang, 2019) proposed a novel WSN based energy-efficient coverage protocol based on a genetic algorithm. A two-dimensional simulation model is proposed to represent a sensing area using the minimum number of sensor nodes. The genetic algorithm incorporated with the k-covered technique to compute the minimum number of potential positions of sensor nodes so that all targets must be covered. The simulated result showed performance enhancement and achieved a high degree of covering the targets with minimum wastage of energy in the network. The use of the proposed protocol in the Dimension area is yet to be implemented and is open for research. The authors (So-In, Nguyen and Nguyen, 2019) presented a distributed deployment protocol to enhance WSN area-coverage called coverage hole-healing algorithm (CHHA). The working of the protocol is divided into two stages. In the first stage a novel approach called Delaunay triangulation topology proposed for detecting hole-boundary nodes. In the second stage a hole healing algorithm is used to track the movements of the nodes in the network to heal the coverage hole with minimum moving distance. The three parameters are used in the simulation are the number of SNs moved, the movement distance, and the overall energy consumption of movement where the protocol outperformed better results than existing algorithm. It is also suggested to enhance for global optimization of protocol using soft-computing techniques.
The authors (Khan and Nguang, 2021) proposed a dual-sensing algorithm, a modified version of a previously built technique for sensing and scheduling in road networks. In such a network, the targets can enter from either side of the road. The algorithm proceeds with scanning the road with a two-way scan wave. This approach reduces half of the detection time in the network compared to the existing technique. One drawback here is that it decreases network lifetime. The algorithm is compared to other schemes such as duty cycling and always-awake schemes. In addition, a comprehensive labeling scheme base hole healing algorithm is proposed in the road network.
The authors (Xu, Jiao and Tian, 2020) proposed an efficient optimization methodology by combining the node scheduling with the routing protocol. The new algorithm is proposed in order to avoid redundant coverage and find out the minimum number of nodes in the network. To overcome the issue of dead nodes, a wake-up scheme is also proposed to activate only appropriate nodes replaced with the dead nodes. Optimized energy consumption in data communication is achieved in the proposed protocol using a minimum coverage set incorporated with the new routing protocol. The CH selection task is performed by considering the residual energy of nodes, distance to the sink node, and the probability of the node. To balance the energy consumption in the networks, a few uneven clusters are also formed in the proposed protocol. The proposed protocol needs some changes in order to adapt to the unreliability of the WSN channel that may lead to data missing due to transmission failure. The proposed algorithm must be combined with efficient channel encoding or such kind of data retransmission schemes in real scenarios.
The authors (Verma and Sharma, 2018) proposed a decentralized localization algorithm for the detection and restoration of coverage holes in WSN. The proposed algorithm is called the Coverage Hole Detection and Restoration algorithm. Energy and time are the key parameters that are improved to enhance the overall performance of the network. Convex and non-convex holes are overcome in the proposed work. The concept of intersection point-based detection and restoration process of coverage hole is demonstrated in the work where a smaller number of patch nodes were used. The advantage of this algorithm is that it can be applied to any kind of area (polygon).
3. Coverage Optimization and Resolve Hole Healing (CHOP) Protocol
The Ψ * Ψ m2 network area and the BS are situated in the middle of the network. The working phases of the proposed protocol are Initialization of the Network, Formation of the Cluster, Selection of Cluster Head, and sleep and wake-up phase. The issues are optimized, and maximum coverage is achieved for a specific sensing range. Using statistics and probability theory, a link is established between the radius of SN and the coverage area. The protocol used the sleep and wake phase to select the minimum number of nodes active to achieve maximum coverage. The CH node aggregates the data and sends it to the BS.
3.1. Initialization of the Network
The 150 sensor nodes are randomly distributed in the Ψ * Ψ m2 network area for the simulation purpose. The simulation is performed for 6000 rounds of packet transmission. The position of BS is the middle in the network. The notation and description are shown in Table 1.
Table 1. Notation and description
S. No. |
Notation |
Definition |
1 |
Ψ |
Network Region |
2 |
SN |
Nodes |
3 |
λ |
PD density |
4 |
PD |
Poisson Distribution |
5 |
lb |
Lower limit [0, k-1] |
6 |
hb |
Upper limit h ≥ 0 |
7 |
SR |
Sensing radius |
8 |
CP |
Coverage Probability |
9 |
CR |
Communication radius |
10 |
Φ |
Area of detection |
The CHOP protocol assumptions.
• The SN is distributed randomly.
• The SN, BS, and CH are all in sync with one another.
• The position of BS is fixed and continuous supply power.
• The nodes have limited battery power.
• The noise factor and signal interference are disregarded.
• In the network region, we are considering 150 effective nodes.
3.2. Formation of the Cluster
The SN gathers data from the environment either individually or in interaction with other SN. Clustering is a method that divides SN into various, and data is transmitted to BS.
The following are some definitions:
Definition 1. Connectivity: The network region (Ψ * Ψ m2) is covered by SN number of Sensor Nodes. The communication and sensing radius of SN is CR and SR, respectively. Thus, the essential condition to maintain the connectivity is:
Definition 2. Coverage: The Sensor Node SN position is adjusted by a stationary Poisson point distribution. The Poisson Distribution (PD) is:
Where λN×P, i.e., the PD density. The value of N is large, that is, the number of Sensor Nodes (SN) in the area of detection Φ and SN >> 10. The value of P is small and is defined as coverage probability (CP). The CP is the ratio of the area of sensing to the area of detection Φ and CP << 0.1.
Let «α» be the network coverage probability value. The neighboring nodes of SN in the Φ can attain the value «α» in the interval of [r - lb, r + hb].
Substituting the λ in Eq. (2),
Where
The partial derivative is calculated with respect to SR.
To achieve maximum coverage at sensing radius SR, set the partial derivative to zero.
Then,
When the SN is confirmed, then SR is taken from the above Eq. (15) in the interval [r-lb, r+hb] to achieve a higher coverage probability for the network.
A set of SN, Ω = {S1, S2, …, SN} covering the network area (Ψ) where SN(i) is an individual sensor that belongs to Ω and i ∈ [1, 2, 3…, 150]. The 150 SN are distributed randomly in the 100 * 100 m2 network area. The target points P = {P1, P2, …, PM}is to be covered. The D (Si, Pj) denotes the distance between the (SN(i), P(j)). The coverage function F(P) is defined as:
Eq. (17) represents the binary value of the coverage function, where 1 indicates that P is covered by SN(i). At the same time, P can be covered by multiple SN(i). If P is covered by k number of SN(i) then F(P) = k. The coverage of the network with respect to the deployed SN(i) is computed as:
Thus, Eq. (18) is also known as a function of network coverage. The F(Ψ) is described as the least value of f(D(Si, P)) for all the possible values of P in Ψ.
3.3. Selection of Cluster Head
The selection of CH is chosen among the active Sensor Nodes. The CH selection depends on two parameters, i.e., Distance and Energy. The CH aggregates all data and transmit it to BS. The CH selection by using Eq. (19).
Where c is constant, Dmax is Maximum Distance, Dmin is Minimum Distance, DBS is Distance to BS, RE is Residual Energy, IE is Initial Energy.
Algorithm 1. Cluster Head Selection
Initialization: SN = Sensor Nodes, CN = Clusters Number, BS = Base Station, RE = Residual Energy, IE = Initial Energy, Dmax = Maximum Distance, Dmin = Minimum Distance, DBS = Distance to BS, c = constant, CH = Cluster Head, CM = Cluster Member, SR = Sensing radius, Φ = Detection area, CP = Coverage Probability, λ = Poisson Distribution Density T = Threshold.
1: Initialize parameters SR, Φ, CP, SN.
2: Calculate
3: Calculate λ = SN × CP
4: Calculate SR for max CP.
5: for each CH(i) 1: CH do
6:for each SN(j) 1:SN do
7:RE = Calculate Residual Energy (SN(j))
8:Dmax = Calculate Distance (SN(j))
9:End for
10: End for
11: for each SN(i) 1:SN do
12:Calculate
13:T←rand (0,1)
14:if (CH(i) > T)
15:CH = CH_Node (SN(i))
16:else
17:CM = CM_Node (SN(i))
18:End if
19: End for
3.4. Sleep and Wake-up
The Sensor Nodes are preserved in sleep mode to conserve the energy of the network. The network area is initially covered by wake-up nodes, and after a period of time, when the wake-up nodes' energy is completely exhausted, the sensor nodes in the sleep mode are turned on. There are four steps in the sleep and wake-up scheduling technique. In the first step, redundant sensor nodes are switched to sleep mode. In the second step, the common or overlapping area is minimized. In the third step, the radius of each node is increased up to the threshold value. In the fourth step, the sleeping nodes are turned on when the wake-up nodes' energy is completely exhausted.
Step 1: The redundant nodes are switched to sleep mode. The following condition identifies the redundant nodes. Let us consider three intersecting sensor nodes SN1, SN2, SN3. The node SN3 is redundant if the value of the threshold, i.e., 30% of the radius of SN1 is greater than or equal to the distance between (SN1, SN2) and (SN1, SN3) as shown in Figure 1.
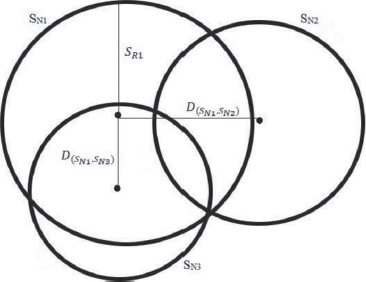
Figure 1. Redundant Sensor Nodes
Step 2: The common area is minimized. The common area is calculated as:
Where common area is denoted as AC, SR1 is the radius of SN1, SR2 is the radius of SN2, and D (SN1, SN2) is the distance between sensors SN1 and SN2. The Nodes lying within the SR of other SN are identified and switched to sleep mode. For example, if SR1 is greater than or equal to the D (SN1, SN2), then node SN2 lies within the sensing radius of node SN1. Thus, node SN2 is switched to sleep mode.
Step 3: Each node's radius is increased until it reaches a threshold value of 25% of its initial radius, at which point it intersects the border of a neighbor node.
Step 4: When the energy of the wake-up nodes is totally exhausted, the sleeping nodes are turned on.
Algorithm 2. Sleep and Wake-up Scheduling
Initialization: SN = Nodes, IN = Intersect Nodes, SR(i) = Radius, SNR(i) = Nodes with Radius SR(i), DPQ(i) = Distance between sensor P and Q LT = Lifetime, Cl = Common length, NN = Nearest Neighbor Node.
1: for node 1: SN do
2:if (DPQ(i) ≤ (SR(i) * 0.3))
3:Sleep (SNR(i))
4:End if
5: End for
6: for in 1: SN do
7:SR(i) = SR(i) – min (C1, C2, C3---------Cl)
8: End for
9: for Node 1: SN do
10:if (DPQ(i) ≤ SR(i))
11:Sleep (SNR(i))
12:End if
13: End for
14: for Node 1: SN do
15:SR(i) = SR(i) + SNR(i) × 0.25
16: End for
17: for every non –intersect node
18:SR(i) = SR(i) + 1;
19: End for
20: for Node 1: SN do
21:if (LT == 0)
22:Awake (NN)
23:End if
24: End for
4. Simulation Performance and Validations
Simulation is performed in MATLAB software. Table 2 value (Narayan and Daniel, 2021) is used for the proposed protocol simulation parameter. The simulation for a network lifetime of 150 nodes is performed for a 100*100 m2 network area. The lifetime is evaluated for successfully 6000 rounds of packet transmission. The proposed protocol is contrasted with LEACH, DEEC, TEEN, and SEP protocols in terms of network performance and packet successfully transmitted to BS. The CHOP improves the system performance for the validation of research work (Mohamed, Khalil and Hammad, 2018).
Table 2. Simulation Value (Narayan and Daniel, 2021)
Symbol |
|
Values |
Ψ |
Network Region |
100 m2 |
SR |
Sensing radius of Node |
Four units |
ETX |
Energy for Transmission |
50nj//bit |
EDA |
Energy for Aggregation |
5//nj/bit |
P |
CH Selection Probability |
0.1 |
Eamp |
Dissipation Energy |
10 pJ//bit/m2 |
Efs |
Amplifier power consumption (d<d0) |
10 pJ//bit//m2 |
Erx |
Amplifier energy consumption(d≥d0) |
0.0013pJ//bit/m4 |
E0 |
Initial energy per node |
0.50 Joule |
4.1. LEACH and CHOP-LEACH Network Lifetime
The simulation result in Figure 2 shows that the CHOP-LEACH protocol achieves a better stability period and improves network performance compared with the LEACH protocol. The first packet drop indicates that the network will be unstable for LEACH protocol at 1499 rounds and the CHOP-LEACH at 2031 rounds. The LEACH protocol lifetime is 3099 rounds, whereas CHOP-LEACH is 3956 rounds.
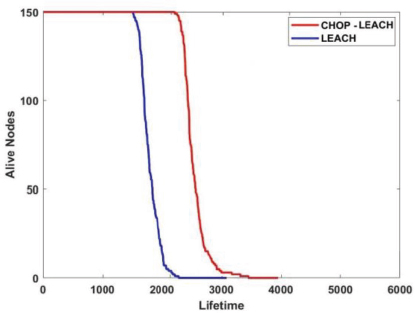
Figure 2. LEACH Vs. CHOP-LEACH
4.1.1. LEACH Vs CHOP-LEACH Packet transmitted to BS
The CHOP-LEACH utilizes optimal energy consumption inside the network, enhances node residual energy, and transmits more packets to BS. The 2.6 × 104 packets are transmitted by LEACH protocol, whereas 3.4 × 104 packets are transmitted by CHOP-LEACH to BS are shown in Figure 3.
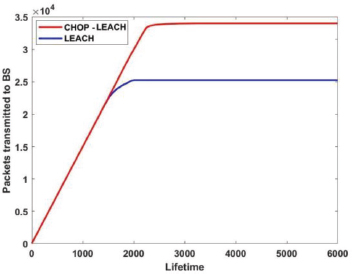
Figure 3. LEACH Vs. CHOP-LEACH
4.2. TEEN and CHOP-TEEN Network Lifetime
The simulation performance in Figure 4 shows CHOP-TEEN protocol achieves a better stability period and improves network performance compared with the TEEN protocol. The first packet drop indicates that the network will be unstable for TEEN protocol at 2121 rounds and the CHOP-TEEN at 2311 rounds. The TEEN protocol lifetime is 4699 rounds, whereas CHOP-TEEN is 5073 rounds.
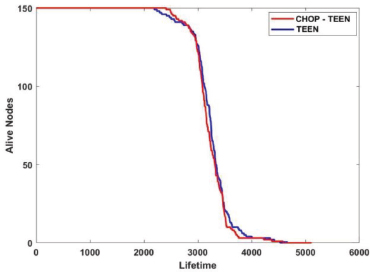
Figure 4. TEEN Vs. CHOP-TEEN
4.2.1. TEEN Vs CHOP-TEEN Packet transmitted to BS
The CHOP-TEEN utilizes optimal energy consumption inside the network, enhances node residual energy, and transmits more packets to BS. The 3.1 × 104 packets are transmitted by TEEN protocol, whereas 3.4 × 104 packets are transmitted by CHOP-TEEN to BS is shown in the Figure 5.
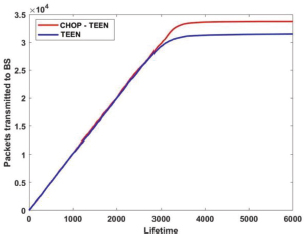
Figure 5. TEEN Vs CHOP-TEEN
4.3. SEP and CHOP-SEP Network Lifetime
The simulation result in Figure 6 shows that the CHOP-SEP protocol achieves a better stability period and improves network performance compared with the SEP protocol. The first packet drop indicates that the network will be unstable for SEP protocol at 1420 rounds and the CHOP-SEP at 2110 rounds. The SEP protocol lifetime is 4051 rounds, whereas CHOP-SEP is 5251 rounds.

Figure 6. SEP Vs. CHOP-SEP
4.3.1. SEP Vs CHOP-SEP Packet transmitted to BS
The CHOP-SEP utilizes optimal energy consumption inside the network, enhances node residual energy, and transmits more packets to BS. The 3.2 × 104 packets are transmitted by SEP protocol, whereas 3.9 × 104 packets are transmitted by CHOP-SEP to BS is shown in Figure 7.
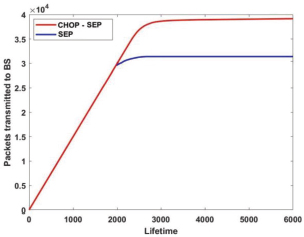
Figure 7. SEP Vs CHOP-SEP
4.4. DEEC and CHOP-DEEC Network Lifetime
The simulation result in Figure 8 shows that the CHOP-DEEC protocol achieves a better stability period and improves network performance compared with the DEEC protocol. The first packet drop indicates that the network will be unstable for the DEEC protocol at 2101 rounds and the CHOP-DEEC at 2231 rounds. The DEEC protocol lifetime is 4701 rounds, whereas CHOP-DEEC is 5050 rounds.
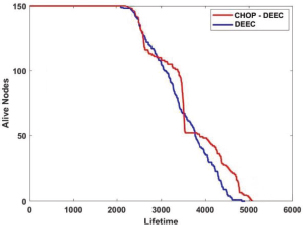
Figure 8. DEEC Vs. CHOP-DEEC
4.5. DEEC Vs CHOP-DEEC Packet transmitted to BS
The CHOP-DEEC utilizes optimal energy consumption inside the network, enhances node residual energy, and transmits more packets to BS. The 1.4 × 105 packets are transmitted by DEEC protocol, whereas 2.2 × 105 packets are transmitted by CHOP-DEEC to BS is shown in Figure 9.
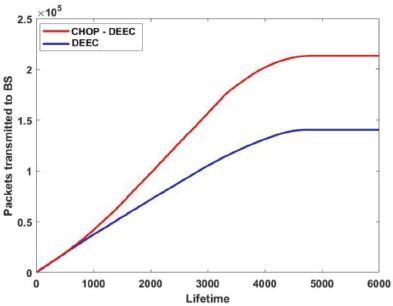
Figure 9. DEEC Vs CHOP-DEEC
The performance of CHOP Protocol for the First Packet Drop (FPD), Last Packet Drop (LPD), and the number of packets successfully transmitted to station node is shown in Figure 10. Table 3 shows that the simulation performance of CHOP protocol in terms of FPD, LDP, and packet transmitted to BS.
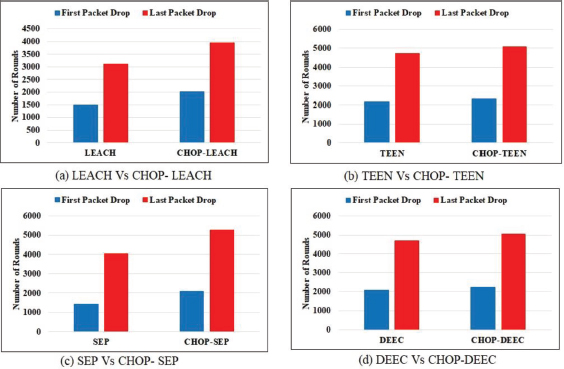
Figure 10. Simulation Performance for the first packet and the last packet drop for 150 nodes
Table 3. Simulation Performance Table
Routing Protocol |
LEACH |
CHOP-LEACH |
TEEN |
CHOP-TEEN |
SEP |
CHOP-SEP |
DEEC |
CHOP-DEEC |
FPD |
1499 |
2031 |
2121 |
2311 |
1420 |
2110 |
2101 |
2231 |
LPD |
3099 |
3956 |
4699 |
5073 |
4051 |
5251 |
4701 |
5050 |
Packet to BS |
2.6×104 |
3.4×104 |
3.1×104 |
3.4×104 |
3.2×104 |
3.9×104 |
1.4×105 |
2.2×105 |
The overlapping of nodes and coverage hole issues is minimized. The proposed protocol CH selection is based on minim BS distance and maximum node RE. The sleep and wake-up concept is used to keep the minimum no of nodes to be active and adjust the load distribution across the network.
5. Conclusion and Future Work
In this paper, we have focused on two fundamental issues that are overlapping of nodes and the coverage hole problem. The CHOP protocol is proposed to overcome the issues. The sleep and wake-up technique is used to cover the network with minimum active nodes and adjust the load distribution across the network. The Poisson distribution function is applied for maximum network coverage in the network.The CHOP protocol is contrasted with traditional routing protocols such as LEACH, TEEN, SEP, DEEC and an enhanced lifetime of the network, better stability period, and more data packets successfully to the base station. In the future fuzzy logic, the technique will use for the selection of cluster head. The approach maximizes the coverage area using the optimal number of nodes and efficient energy utilization in the network. The identification and prevention of energy holes are important research problems, will deal with this problem in the future. We will perform an experimental test for the mobile and static sensor networks. In the future, we will also plan to develop techniques for recovering holes with limited mobility of nodes.
References
Al-Fuhaidi, B. et al. (2020) «An Efficient Deployment Model for Maximizing Coverage of Heterogeneous Wireless Sensor Network Based on Harmony Search Algorithm», Journal of Sensors, 2020.
Al-Shalabi, M., Ababneh, J. and Abdulraheem, W. (2021) «A Novel Adjacent Sensors-Based Mechanism to Increase Performance of Wireless Sensor Networks», International Journal of Antennas and Propagation, 2021.
Aliouane, L. and Benchaïba, M. (2016) «Efficient boundary detection of coverage hole in WSNs», in 2016 International Symposium on Networks, Computers and Communications (ISNCC), pp. 1–6.
Aliouat, Z. and Harous, S. (2012) «An efficient clustering protocol increasing wireless sensor networks life time», in 2012 International Conference on Innovations in Information Technology (IIT), pp. 194–199.
Behera, T. M., Samal, U. C. and Mohapatra, S. K. (2018) «Energy-efficient modified LEACH protocol for IoT application», IET Wireless Sensor Systems, 8(5), pp. 223–228.
Cai, S. et al. (2019) «Data collection in underwater sensor networks based on mobile edge computing», IEEE Access, 7, pp. 65357–65367.
Chaturvedi, P. and Daniel, A. K. (2017) «A novel sleep/wake protocol for target coverage based on trust evaluation for a clustered wireless sensor network», International Journal of Mobile Network Design and Innovation, 7(3–4), pp. 199–209.
Chen, Y., Xu, X. and Wang, Y. (2019) «Wireless sensor network energy efficient coverage method based on intelligent optimization algorithm», Discrete & Continuous Dynamical Systems-S, 12(4\&5), p. 887.
Dwivedi, A. K., Sharma, A. K. and Mehra, P. S. (2020) «Energy efficient sensor node deployment scheme for two stage routing protocol of wireless sensor networks assisted iot», ECTI Transactions on Electrical Engineering, Electronics, and Communications, 18(2), pp. 158–169.
Farhat, A. et al. (2018) «On the coverage effects in wireless sensor networks based prognostic and health management», International Journal of Sensor Networks, 28(2), pp. 125–138.
Gupta, G. P. and Jha, S. (2019) «Biogeography-based optimization scheme for solving the coverage and connected node placement problem for wireless sensor networks», Wireless Networks, 25(6), pp. 3167–3177.
El Handri, K. and Idrissi, A. (2020) «Parallelization of Topk Algorithm Through a New Hybrid Recommendation System for Big Data in Spark Cloud Computing Framework», IEEE Systems Journal.
Harizan, S. and Kuila, P. (2019) «Coverage and connectivity aware energy efficient scheduling in target based wireless sensor networks: An improved genetic algorithm based approach», Wireless Networks, 25(4), pp. 1995–2011.
Khan, F. and Nguang, S. K. (2021) «Dual sensing scheduling algorithm for WSN based road network surveillance», AIMS Electronics and Electrical Engineering, 5(1), pp. 38–54.
Khan, M. N. et al. (2020) «Improving energy efficiency with content-based adaptive and dynamic scheduling in wireless sensor networks», IEEE Access, 8, pp. 176495–176520.
Luo, J. and Fu, L. (2017) «A smartphone indoor localization algorithm based on WLAN location fingerprinting with feature extraction and clustering», Sensors, 17(6), p. 1339.
Mittal, N., Singh, U. and Sohi, B. S. (2017) «Harmony Search Algorithm Based Threshold-sensitive Energy-Efficient Clustering Protocols for WSNs.», Adhoc & Sensor Wireless Networks, 36.
Mohamed, M. A., Khalil, A. T. and Hammad, A. (2018) «An energy-efficient wireless sensor network routing protocol powered by ambient energy harvesting», International Journal of Wireless and Mobile Computing, 14(4), pp. 378–386. doi: 10.1504/IJWMC.2018.093861.
Nandagopal, C. and Ramesh, S. M. (2020) «An Efficient Data Gathering Technique Using Optimal Minimum Coverage Spanning Tree Algorithm in WSN», Journal of Circuits, Systems and Computers, 29(14), p. 2050225.
Narayan, V. and Daniel, A. K. (2019) «Novel protocol for detection and optimization of overlapping coverage in wireless sensor networks», Int. J. Eng. Adv. Technol, 8.
Narayan, V. and Daniel, A. K. (2021) «A Novel Approach for Cluster Head Selection using Trust Function in WSN», Scalable Computing: Practice and Experience, 22(1), pp. 1–13.
Narayan, V., Daniel, A. K. and Rai, A. K. (2020) «Energy Efficient Two Tier Cluster Based Protocol for Wireless Sensor Network», in 2020 International Conference on Electrical and Electronics Engineering (ICE3), pp. 574–579.
Nayak, P. et al. (2021) «Routing in wireless sensor networks using machine learning techniques: Challenges and opportunities», Measurement, 178, p. 108974.
Nehra, V., Sharma, A. K. and Tripathi, R. K. (2020) «I-DEEC: improved DEEC for blanket coverage in heterogeneous wireless sensor networks», Journal of Ambient Intelligence and Humanized Computing, 11(9), pp. 3687–3698.
Nithya, R. and Jegadeeshwari, P. (2019) «Design of Novel Based Sensing Model for Coverage Area Using Evolutionary Algorithm».
Peng, H. et al. (2015) «Energy-efficient and scalable clustering scheme for wireless sensor networks», in 2015 International Conference on Wireless Communications \& Signal Processing (WCSP), pp. 1–6.
Prusty, A. R., Sethi, S. and Nayak, A. K. (2020) «Energy aware optimized routing protocols for wireless ad hoc sensor network», in Sensor technology: concepts, methodologies, tools, and applications. IGI Global, pp. 1494–1521.
Rai, N. and Daruwala, R. D. (2016) «Effect of probabilistic sensing models in a deterministically deployed wireless sensor network», in 2016 IEEE Region 10 Conference (TENCON), pp. 1352–1355.
Rajawat, A. S., Jain, S. and Barhanpurkar, K. (2021) «Fusion protocol for improving coverage and connectivity WSNs», IET Wireless Sensor Systems.
Ramluckun, N. and Bassoo, V. (2018) «Energy-efficient chain-cluster based intelligent routing technique for Wireless Sensor Networks», Applied Computing and Informatics.
Salam, T. and Hossen, M. S. (2020) «Performance analysis on homogeneous LEACH and EAMMH protocols in wireless sensor network», Wireless Personal Communications, pp. 1–34.
Shi, K., Chen, H. and Lin, Y. (2015) «Probabilistic coverage based sensor scheduling for target tracking sensor networks», Information sciences, 292, pp. 95–110.
Singh, S. et al. (2020) «Proficient QoS-based target coverage problem in wireless sensor networks», IEEE Access, 8, pp. 74315–74325.
Singh, S. and Malik, A. (2017) «hetSEP: Heterogeneous SEP protocol for increasing lifetime in WSNs», Journal of Information and Optimization Sciences, 38(5), pp. 721–743.
So-In, C., Nguyen, T. G. and Nguyen, N. G. (2019) «An efficient coverage hole-healing algorithm for area-coverage improvements in mobile sensor networks», Peer-to-Peer Networking and Applications, 12(3), pp. 541–552.
Verma, M. and Sharma, S. (2018) «A greedy approach for coverage hole detection and restoration in wireless sensor networks», Wireless Personal Communications, 101(1), pp. 75–86.
Wang, C. et al. (2015) «A mobile data gathering framework for wireless rechargeable sensor networks with vehicle movement costs and capacity constraints», IEEE Transactions on Computers, 65(8), pp. 2411–2427.
Wang, Xiaodong et al. (2010) «Dynamic duty cycle control for end-to-end delay guarantees in wireless sensor networks», in 2010 IEEE 18th International Workshop on Quality of Service (IWQoS), pp. 1–9.
Xu, Y., Jiao, W. and Tian, M. (2020) «Energy-efficient connected-coverage scheme in wireless sensor networks», Sensors, 20(21), p. 6127.
Zimmerling, M., Mottola, L. and Santini, S. (2020) «Synchronous transmissions in low-power wireless: A survey of communication protocols and network services», ACM Computing Surveys (CSUR), 53(6), pp. 1–39.